This comprehensive guide offers a structured approach to assessing third party compliance maturity, drawing on established market standards and best practices. It addresses the challenges businesses face in navigating varying regulations and provides a systematic framework for third party evaluation, ensuring ongoing protection of sensitive data and maintenance of privacy standards.
This guide is focused on third party compliance assessment under regulations and frameworks such as the GDPR, DORA, HIPAA, CCPA, AI ACT, etc.
Understanding the Challenge
While regulations often mandate third party assessments, they rarely provide specific guidelines on conducting these evaluations. This creates a complex landscape where businesses must navigate varying standards across different countries, frameworks and sectors. Each framework often has its own requirement to vendor assessment.
The absence of standardized assessment methodologies further complicates the process, leading to inconsistencies and potential oversights in vendor evaluations.
Our comprehensive guide addresses this challenge by offering a systematic approach to third party compliance assessment, ensuring a consistent and thorough evaluation process regardless of the vendor’s location or industry.
Key Assessment Components
Our approach emphasizes several key components in vendor assessment, including initial data privacy maturity evaluation, compliance documentation deep dive, contractual framework assessment, geographic considerations, supply chain evaluation, and operational controls.
Each component focuses on specific aspects of vendor compliance and data practices, providing a comprehensive understanding of the vendor’s overall compliance posture.
This holistic approach ensures that all critical areas are thoroughly evaluated, minimizing the risk of overlooking potential compliance issues.
Initial Privacy Maturity Evaluation
The first phase involves conducting a high-level assessment of the vendor’s data privacy commitment. This initial assessment sets the stage for more in-depth analysis and helps identify potential red flags early in the assessment process. A vendor’s commitment to data privacy often reflects its organizational culture and overall approach to data protection.
Key indicators include:
- Recent privacy-related incidents or breaches
- Website maintenance and professional presentation of online policies
- Privacy policy update frequency and comprehensiveness
- Presence of a dedicated trust center or privacy/security documentation
- Third-party certifications (ISO/SOC II)
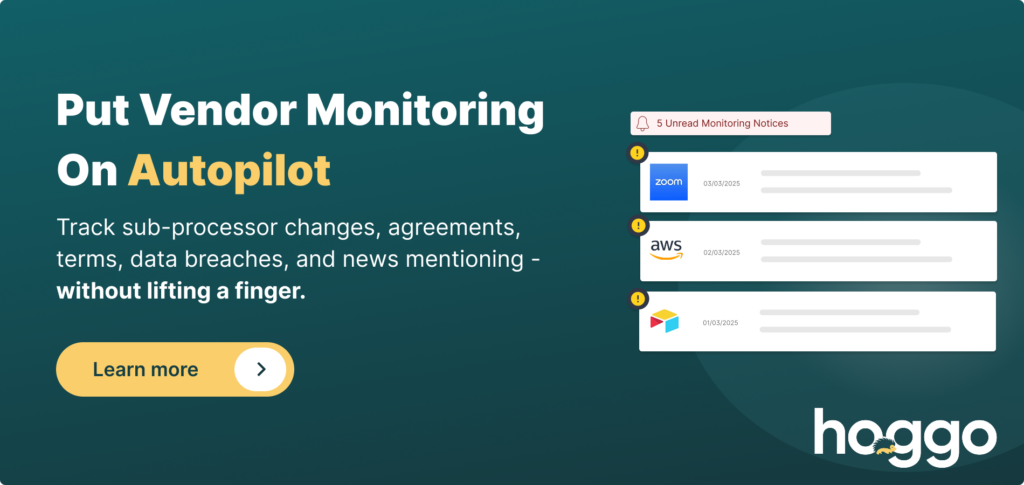
Automate Initial Privacy Maturity Evaluation
There are tools, like hoggo, that automated the privacy maturity assessment process. Additionally, you don’t need to hunt for those vendor documentations, as hoggo centralizes everything for you in one solidified vendor Trust Profile.
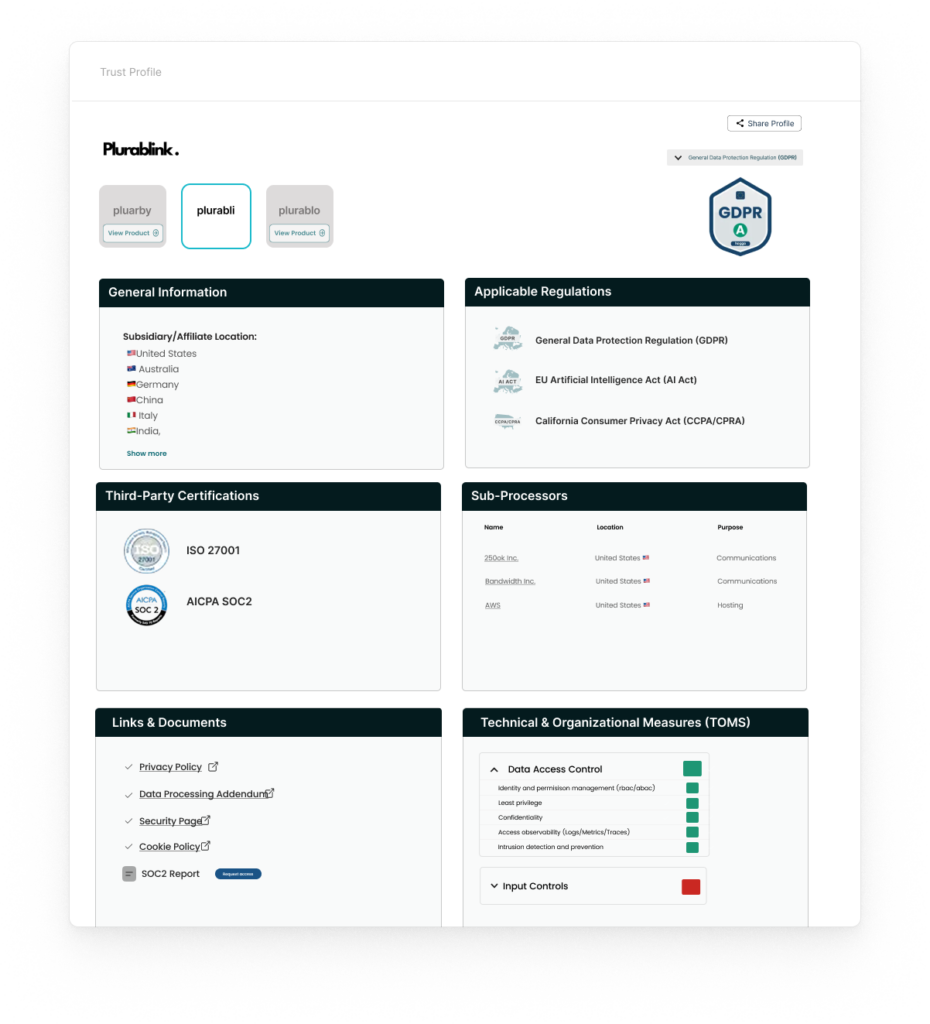
Documentation Deep Dive
A thorough review of the vendor’s compliance documentation reveals their data handling and security practices. This deep dive provides insights into the vendor’s data processing activities, data sharing practices, and commitment to data subject rights. Analyzing the vendor’s policies and related documents enables organizations to assess the vendor’s compliance with relevant regulations and internal policies.
Discrepancies or ambiguities in the documentation may indicate potential compliance issues.
Policies Assessment
Example for Privacy Policy Analysis:
- Types of data collection and purposes
- Data sharing practices and partnerships
- Geographic locations of data transfers
- Data enrichment service utilization
- Legal basis for data processing
- Data subject rights implementation
Contractual Framework Assessment
Data Processing Agreement (DPA) Review:
- Verification of DPA coverage for relevant data types
- Alignment with internal policies and customer obligations
- Review of Technical and Organizational Measures (TOMs)
- Assessment of security certifications and their scope
Automate Documentation Assessment
With hoggo you can easily find all the relevant documents in one Trust Profile. hoggo also provides benchmarks and assessment based on your company’s guidelines and intended use.
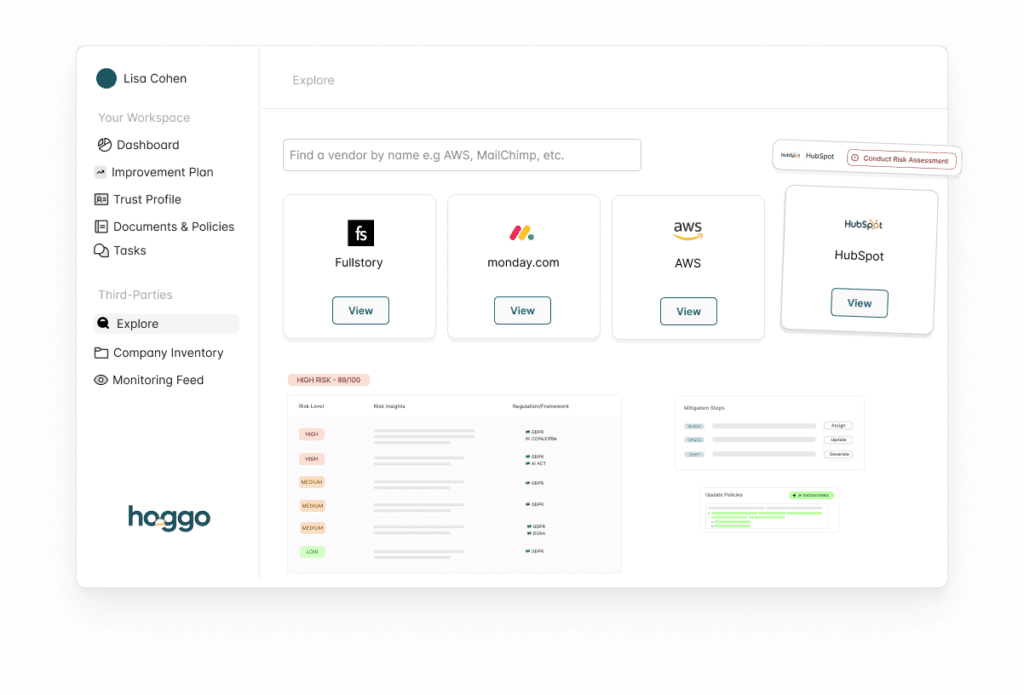
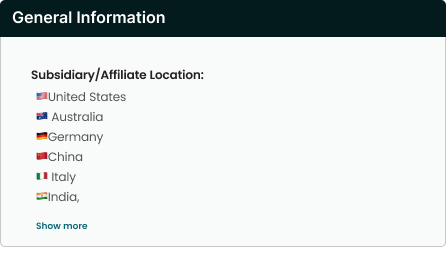
Geographic Considerations
Data privacy regulations, security frameworks and other data-related laws vary significantly across geographic regions, and it’s crucial to consider these differences when evaluating vendor compliance.
Factors such as data localization requirements, transfer mechanisms, and the vendor’s headquarters location can impact the overall compliance posture. A vendor’s ability to adhere to region-specific regulations is a critical indicator of their commitment to data protection.
Location Analysis
- Headquarters location verification
- Data processing locations identification
- Transfer mechanism compliance
- Data localization requirement adherence
Automate Geographic Locations Search
Finding all the HQ, subsidiaries, and processing locations kind be challenging and resource consuming. But skipping this step is a huge risk. Luckily, hoggo does the search for you.
Supply Chain Evaluation
Assessing the vendor’s supply chain is essential, as data often passes through multiple sub-processors or partners.
Understanding the digital supply chain and the geographic distribution of sub-processors is vital for assessing the overall compliance posture.
Transparency in data transfers and the purposes for which data is shared with sub-processors is a critical aspect of vendor evaluation. Incomplete or unclear information regarding sub-processors can indicate potential compliance risks.
Sub-processor Assessment
- Digital supply chain transparency
- Data transfer types and purposes
- Geographic distribution of sub-processors
- Impact on overall compliance posture
Automate Supply Chain Evaluation
Assessing the vendor AND their sub-processors can be time consuming. With hoggo, it’s easy to get an overview of a vendor’s sub-processor list and quickly view and assess their compliance posture.
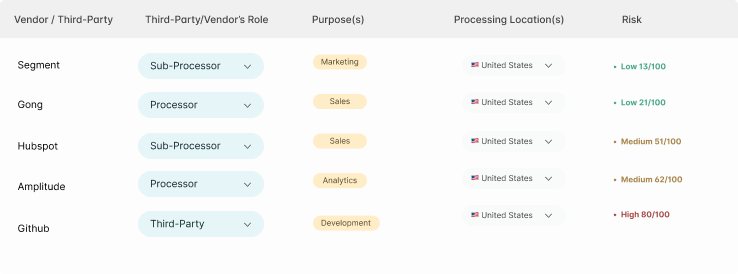
Operational Controls
Evaluating the vendor’s operational controls is essential for ensuring ongoing data protection and compliance. These controls include data retention policies, deletion procedures, employee confidentiality commitments, breach notification protocols, and audit rights. A vendor’s ability to demonstrate effective operational controls is a strong indicator of their commitment to data protection and overall compliance.
Key Operational Elements
- Data retention period definitions
- Data deletion and return procedures
- Employee confidentiality commitments
- Breach notification protocols
- Audit rights and procedures
Automate Operational Control Assessment
Use hoggo to check and verify a vendor’s operational controls easily –
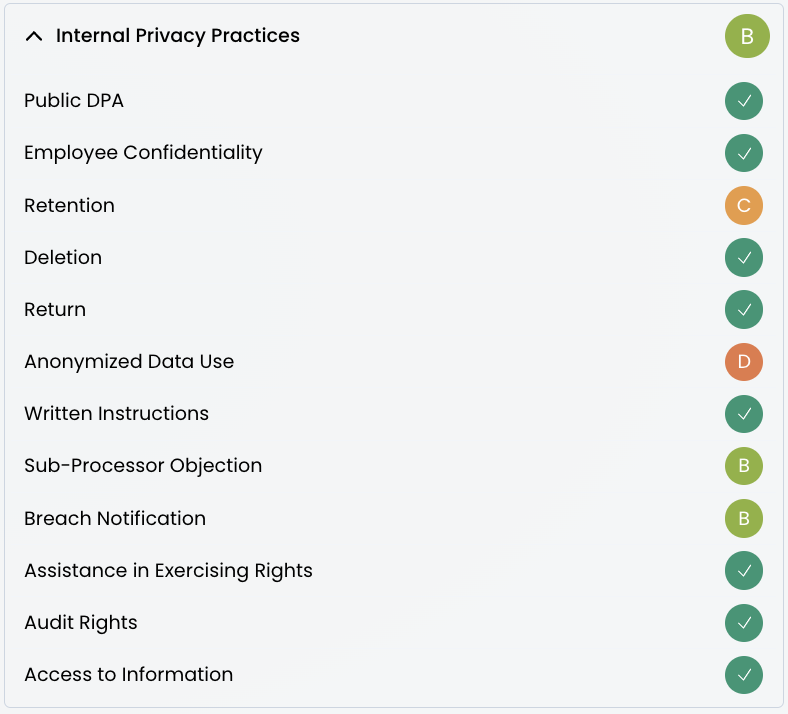
Red Flags in Vendor Compliance Assessment
Identifying red flags during vendor assessment is crucial for mitigating potential compliance risks. These warning signs indicate that the vendor may not have adequate privacy practices in place or may be unwilling to comply with necessary requirements.
Recognizing these red flags early in the assessment process allows organizations to take appropriate action and avoid potential data breaches or regulatory penalties.
Critical Warning Signs
🚩 Immature or uncommitted data handling practices
🚩 Vague language in documentation
🚩 Reluctance to sign standard agreements
🚩 Unclear processing locations
🚩 Limited sub-processor transparency
🚩 Resistance to basic compliance requirements
🚩 Ambiguous responses regarding retention and deletion
Post-Assessment Monitoring
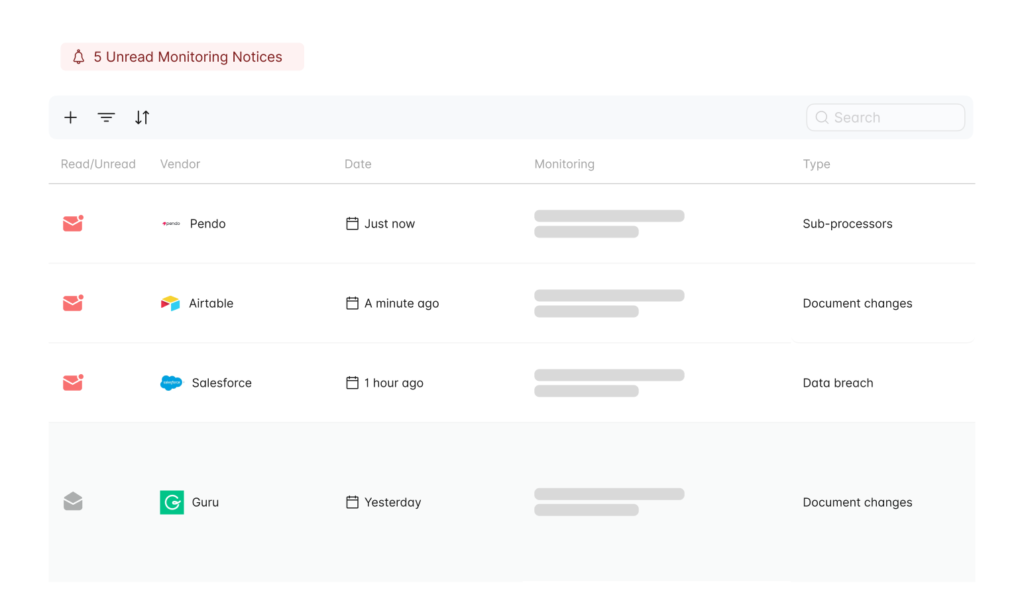
After the initial assessment has been completed and you’ve decided to work with a certain vendor, the compliance evaluation can’t stop there. If you leave that vendor unsupervised, you could miss critical updates that might risk your organizations’ compliance posture. Your compliance is as strong as your weakest links, in this case – vendor.
For this reason, it is crucial to monitor your vendors, check changes to their policies, agreements, terms, sub-processors and even news mentioning. Usually, it takes time from a data breach or an incident until they have to notify you. But the news are usually faster.
Staying on top of vendor risks it’s like having another full time job. We at hoggo offer automated vendor compliance monitoring. hoggo scans vendor updates on a daily basis and posts any important notice on your monitoring feed. Plus, you’ll get a monthly summary directly to your mailbox.
Conclusion
While this checklist provides a robust framework for vendor assessment, it should be adapted to specific organizational needs and regulatory requirements. Regular reviews and updates of vendor compliance status ensure ongoing protection of sensitive data and maintenance of privacy standards. Organizations must stay informed about evolving data regulations and market trends and update their assessment methodologies accordingly. Additionally, continuous monitoring of vendor compliance through regular audits and assessments is essential for mitigating potential risks and maintaining a strong compliance posture.

Noa Kahalon
Noa is a certified CIPM, CIPP/E, and a Fellow of Information Privacy (FIP) from the IAPP. Her background consists of marketing, project management, operations, and law. She is the co-founder and COO of hoggo, an AI-driven Digital Governance platform that allows legal and compliance teams connect, monitor, and automate digital governance across all business workflows.
- Noa Kahalon#molongui-disabled-link
- Noa Kahalon#molongui-disabled-link
- Noa Kahalon#molongui-disabled-link
- Noa Kahalon#molongui-disabled-link