As businesses compete by developing their technologies, the finance industry has experienced remarkable tech-led disruption that has grown dependent on digital infrastructure and services. Before we delve into what your responsibilities are when engaging ICT third-party service providers, let’s take a moment to understand what the Digital Operational Resilience Act (DORA) is all about and why it is crucial to comply with it.
Table of Contents
What Is The Digital Operational Resilience Act (DORA)?
Digital transformation has brought more opportunities and faster solutions but alongside this shift, companies have become more vulnerable to cyberattacks. Although companies heavily invest in cybersecurity, cyberattacks are becoming complex and more sophisticated.
Cybersecurity Ventures predicts that global cybercrime costs will exceed US$10tn by 2025. According to CERT-EU’s 2023 Threat Landscape Report, the financial industry was among the top 10 targeted sectors most frequently attacked in 2023, with the exception of attacks in the public administration sector. High-profile hacks that targeted governments and companies resulted in the loss of billions of dollars and the compromising of millions of customer records. In 2020, Norway’s state-owned investment fund lost $10m from a business email compromise scam. To pull off this heist, the scammers gained access to the fund’s email servers and monitored the fund’s communications for several months.
To further protect the EU’s financial sector, the European Parliament in 2022 introduced DORA. It aims to strengthen the IT security of financial institutions in Europe by establishing a consistent regulatory framework to improve operational resilience, ensuring that businesses can resist, respond and recover from ICT-related disruptions. It also provides standardised guidelines for financial entities to follow when developing their internal ICT risk management strategies. This is to ensure that entities may continue to operate despite the cyberattack disruptions. It can also help to reduce financial losses and protect the data of their customers.
Although DORA came into force on 16 January 2023, organizations were required to start applying the requirements from January 17, 2025. The two-year buffer period allowed businesses to prepare for and implement the necessary changes.
Third-Party Compliance Under The Digital Operational Resilience Act (DORA)
According to the European Union Agency for Cybersecurity (ENISA), third-party and supply chain risks pose serious cybersecurity threats, especially when the attacks target software dependencies. This is problematic because supply chain breaches can result in massive data breaches, monetary losses, disruption in services and harm to several firms’ reputations.
Therefore to improve supply chain security and resilience against evolving cyber threats, EU lawmakers have enacted a number of laws in the last few years, including the GDPR, NIS2 Directive and EU AI Act. There are six main pillars of DORA but we will focus on those relating to third-party and supply chain risks.
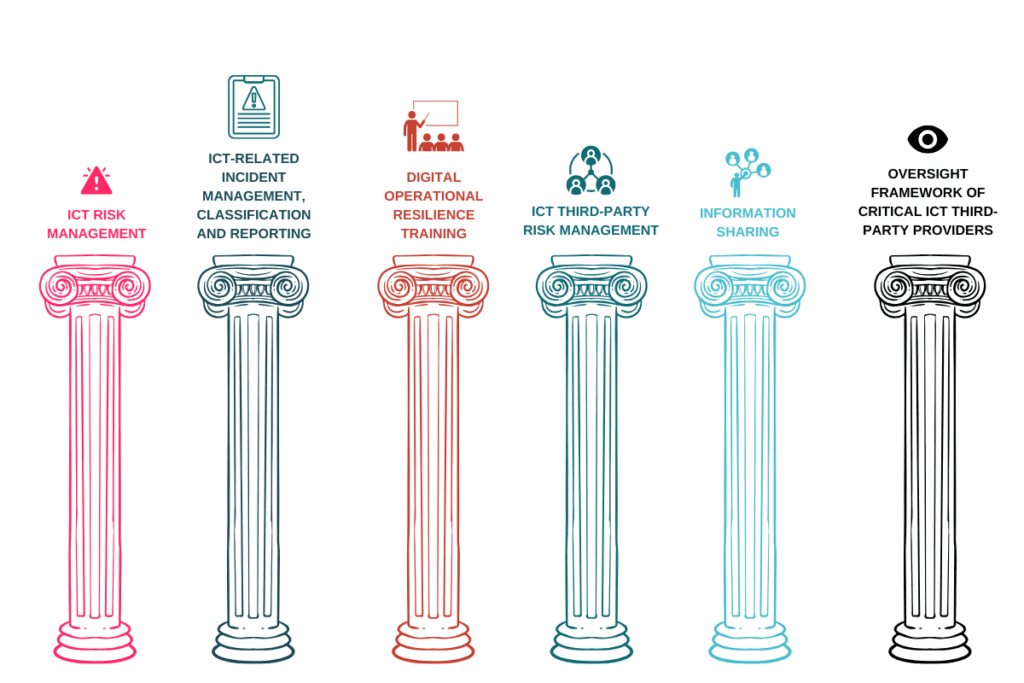
Under DORA, companies must treat risks that are brought by third-parties as their own. Therefore it is important to consider the following when engaging with third-party service providers.
Stage 1: Before Selecting a Third-Party Service Provider
- Due Diligence: Conduct comprehensive due diligence. It is important to look at the third-party provider’s ability to deliver the services reliably, securely and in line with the regulatory expectations.
- Resilience Testing: Test the ICT third-party providers’ operational resilience capabilities by conducting simulations of stress tests to see how the third-party can handle the cyber-attack. This can be done before or after selecting the third-party service provider.
Stage 2: Drafting the Contract
- The contract should include provisions on risk management to ensure that the third-parties (including its sub-contractors) are held accountable for mitigating risks and can continue to provide the service despite the disruption.
- Termination rights should be included to allow the financial entity to exit if the third party fails to comply with the regulatory and operational requirements.
- An exit plan should be reviewed and tested. It should take into account unforeseen and persistent service interruptions, inappropriate or failed service delivery and unexpected termination of the contract.
- The entity must have a clear written transition plan if the third-party service provider isn’t available; rehearse exit strategies by running drills, testing backups; and maintain operational resilience so that operations may continue even after a cyber-attack.
Stage 3: Incorporating a Third-Party Risk Policy in the Risk Management Framework
- Financial entities have to adopt and regularly review their ICT risk management framework by ensuring it has policies relating to third-party ICT service providers (including intra-group service providers and subcontractors) who provide ICT services that support critical functions.
- The degree of obligations and risk exposure will be proportionate to the impact and criticality of the third-party service provider on the financial entity.
- Create and maintain a register of all ICT-third party providers and services. The register should include details about the contracts, the critical or important service(s) provided and risk assessments. This has to be regularly updated and available for regulatory review.
- The management body that is responsible for managing the financial entity’s ICT risk management should continuously control, monitor, adopt and review the Policy at least once per year.
- The policy should identify the role or member of a senior management for monitoring the contractual arrangements.
- The policy has to clearly specify and identify the internal responsibilities for the approval, management, control and documentation of contractual arrangements on the use of ICT services supporting critical or important functions provided by the third-party service provider.
- The policy should include that the due diligence process includes an assessment of the existing risk mitigation and business continuity measures and how the function of the ICT third-party service provider is ensured.
- The policy should also outline that the functions provided by the ICT third-party service providers will be subject to independent review and included in the audit plan.
- The Policy will provide a guideline for the due diligence process in selecting and assessing the prospective ICT third-party service providers and indicate which elements to be used for the required level of assurance on the ICT third-party service provider’s performance.
Stage 4: Post-signing of Contract
- Continuously monitor and ensure that the service provider maintains the expected level of operational resilience and compliance with security standards.
- Monitor concentration risks of ICT third-party providers. It is safe to have contingency plans to address any potential cyber disruptions.
- Recovery and Contingency Plans: Entities should analyse different third-party risk scenarios to develop recovery and contingency plans to handle each disruption.
- If the financial entity discovers any shortcomings of the ICT third-party service providers, it should include in the Policy the appropriate measures to handle the situation and how the measures are to be implemented.
It is important to note that ICT intra-group service providers that are part of the financial entity (e.g. subsidiaries or affiliates) are to be treated as external third-party providers even though the risks posed by the intra-group service providers are different. Additionally, the Policy also applies to intra-group service providers and subcontractors of third-party providers. This ensures that the risks from all providers are properly managed and scrutinized fairly.
Conclusion
Managing third-party risks and ensuring that it is compliant with the various EU laws is crucial especially since the financial entities are increasingly becoming more reliant on external third-party service providers.

Monica Aguilar
Monica is a legal and business professional with a diverse background in law, media, and corporate governance. Her career began in journalism, where she worked as a radio host, TV and print business journalist, and television producer, before transitioning into commercial law. As a barrister and solicitor in Fiji, she advised on corporate governance, foreign investment, mergers and acquisitions, contract law, and regulatory compliance.
- Monica Aguilar#molongui-disabled-link
- Monica Aguilar#molongui-disabled-link
- Monica Aguilar#molongui-disabled-link
- Monica Aguilar#molongui-disabled-link




