The objective of vendor risk management (VRM) is to manage the entire relationship with vendors, from due diligence to privacy risk assessment to business continuity planning.
What is Vendor risk management (VRM)?
According to Gartner, Vendor Risk Management (VRM) is the process of ensuring that the use of service providers and IT suppliers does not cause unacceptable disruptions to the business or negatively impact its performance. As organizations assess, monitor, and manage their risk exposure from third-party vendors who provide IT products and services or have access to the organization’s data, VRM technology supports them.
How to effectively do vendor risk management?
The purpose of vendor risk management (VRM), which falls under vendor management, is to identify, analyze, monitor, and mitigate the risks posed by third-party vendors. Cybersecurity, privacy, regulatory compliance, business continuity, and organizational reputation could be affected by such risks.
Managing vendor risks is an ongoing process, beginning with a vendor risk assessment during onboarding. Managing and monitoring vendor risks continues until vendor offboarding, which ensures that the vendor has no access to databases or personal data and does not pose any risks to the company.
Read more about Vendor Risk Assessments

Vendor Assessment: Data Privacy Due-Diligence
Third parties and vendors for risk management
Typically, third-party vendors provide products or services to your company that are not provided by your company itself. Below are some of the more common types of third-party vendors.
- Suppliers: Depending on your sector, you might be dependent on different companies for your physical suppliers, manufacturers, etc.
- Service Providers: including accountants, lawyers, marketing and advertising agencies, business and management consultants, logistics companies, SaaS services you use, etc.
- Contractors (short term and long term): Contractors make up an increasingly large part of operational teams. This could be tech or IT staff, coders and designers who do not have an employee agreement (external staff and freelancers).
- Partners: This includes business partners or other entities with whom the company has a partnership agreement with.
Why Is Vendor Risk Management Important?
Companies share vast amount of data with their vendors and third-parties. In particular, sharing personal data and confidential data, might expose the company to security and privacy risks.
Therefore, it’s crucial to ensure that the vendor or third party can provide sufficient guarantees to protect such data.
An effective vendor risk management program can reduce the harm of disruptive events and improve a company’s overall privacy and security posture.
It is important to recognize that VRM offers more than reducing risks. For instance, by putting the right tools in the hands of the right people, companies can quickly evaluate and onboard new suppliers.
In addition, a vendor risk program can allow organizations to monitor their supplier relationships over time, identify new risks, and measure supplier performance. There are many other reasons why supplier risk management is essential, including the ability to enforce contracts, reduce spending, and track security controls.
A company faces a number of risks when it engages third parties to handle confidential, sensitive, commercial data or personal data. Your third-party vendors can pose a huge privacy risk regardless of how good your internal privacy controls are if they have poor privacy practices.
Here are some examples of vendor risks:
- Your company may be exposed to legal or compliance risks if you let them access personal data of customers, users, employees, or if you provide financial services.
- As part of the Health Insurance Portability and Accountability Act (HIPAA), Business Associates (BA) also have to protect protected health information (PHI) securely.
- You should know how much information a vendor should be able to access and has access to, and whether they have the means to protect confidential information and avoid security risks.
- If a vendor has access to proprietary information, there is a risk they will steal it or expose it through a data breach, leading to IP risks.
- Reputational risks exists in cases where a data breach or bad practices of your third party vendors expose your users or customers and thus affect your brand image and cause them to move on to your competitors.
When Should Vendors Be Assessed?
Prior to engaging with a vendor, during engagement, and during offboarding, vendor risk assessments should be conducted.
The maturity of the vendor’s privacy and security practices and its ability to protect confidential and personal data must be checked when selecting a vendor. Ensure the vendor has adequate organizational and technological measures to comply with privacy regulations, such as the GDPR.
In order to minimize risks to the company’s data, users, and brand image, it’s important to continuously monitor vendor policies and data breaches after they have been onboarded.
It is important to conduct a vendor risk assessment during the offboarding process when the vendor engagement is nearing its end.
A company should ensure that the vendor has no access to the company’s databases, confidential information, or personal data after the vendor has been offboarded. It is still important to monitor future breaches after offboarding has been completed and examine if the breach time does not correspond to the usage periods.
How hoggo Can Help You Manage Vendors Risks
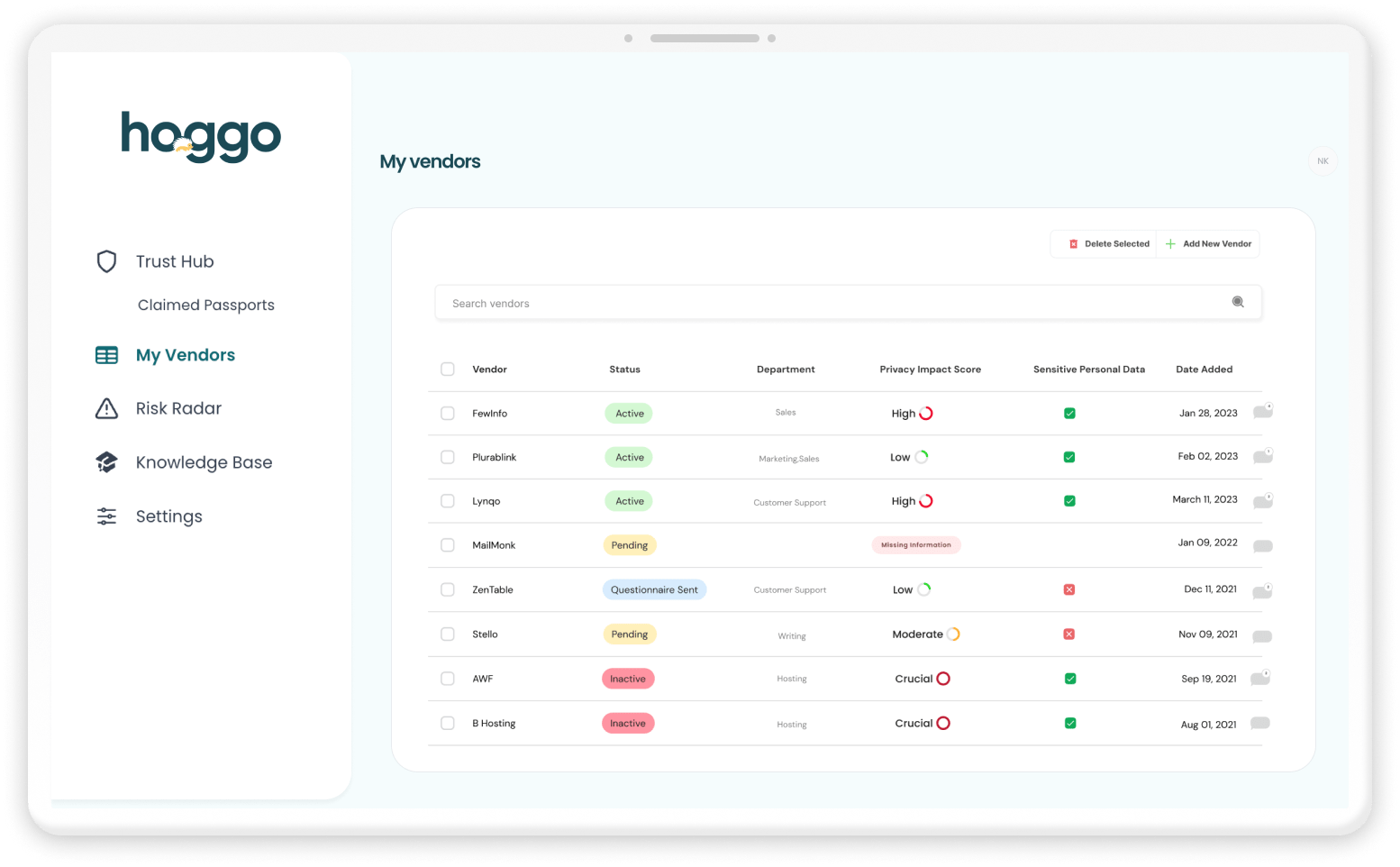
Hoggo allows you to easily conduct vendor risk management (VRM) with My vendors.
By using My Vendors, you can manage your third-party vendors and remove the hassle from vendor privacy risk management. It streamlines workflows to reduce manual assessments and assure consistency.
Hoggo monitors vendor compliance and alerts you to any changes to their policies or data breaches. In addition, our Trust Hub vendor directory can help you identify high-risk vendors and find trustworthy ones.
Hoggo automates vendor risk management, so your team can work on more critical tasks. Freed from the burden of spreadsheets, your business will be able to thrive.

Noa Kahalon
Noa is a certified CIPM, CIPP/E, and a Fellow of Information Privacy (FIP) from the IAPP. Her background consists of marketing, project management, operations, and law. She is the co-founder and COO of hoggo, an AI-driven Digital Governance platform that allows legal and compliance teams connect, monitor, and automate digital governance across all business workflows.
- Noa Kahalon#molongui-disabled-link
- Noa Kahalon#molongui-disabled-link
- Noa Kahalon#molongui-disabled-link