What is A Vendor Assessment?
The purpose of Vendor Assessments is to evaluate how vendors (third-parties) handle the personal data that companies share with them. This assessment helps determine whether vendors are maintaining adequate security and privacy controls.
Vendor Assessments are usually part of a dedicated procedure that aim to ensure that any vendor the company engages with is inline with the company’s security and privacy requirements. During this procedure, companies will ask vendors to demonstrate that they have robust privacy practices in place to securely manage data, and they will review their security and privacy practices.
Third-Party Risk Management (TPRM) Vs. Vendor Assessment?
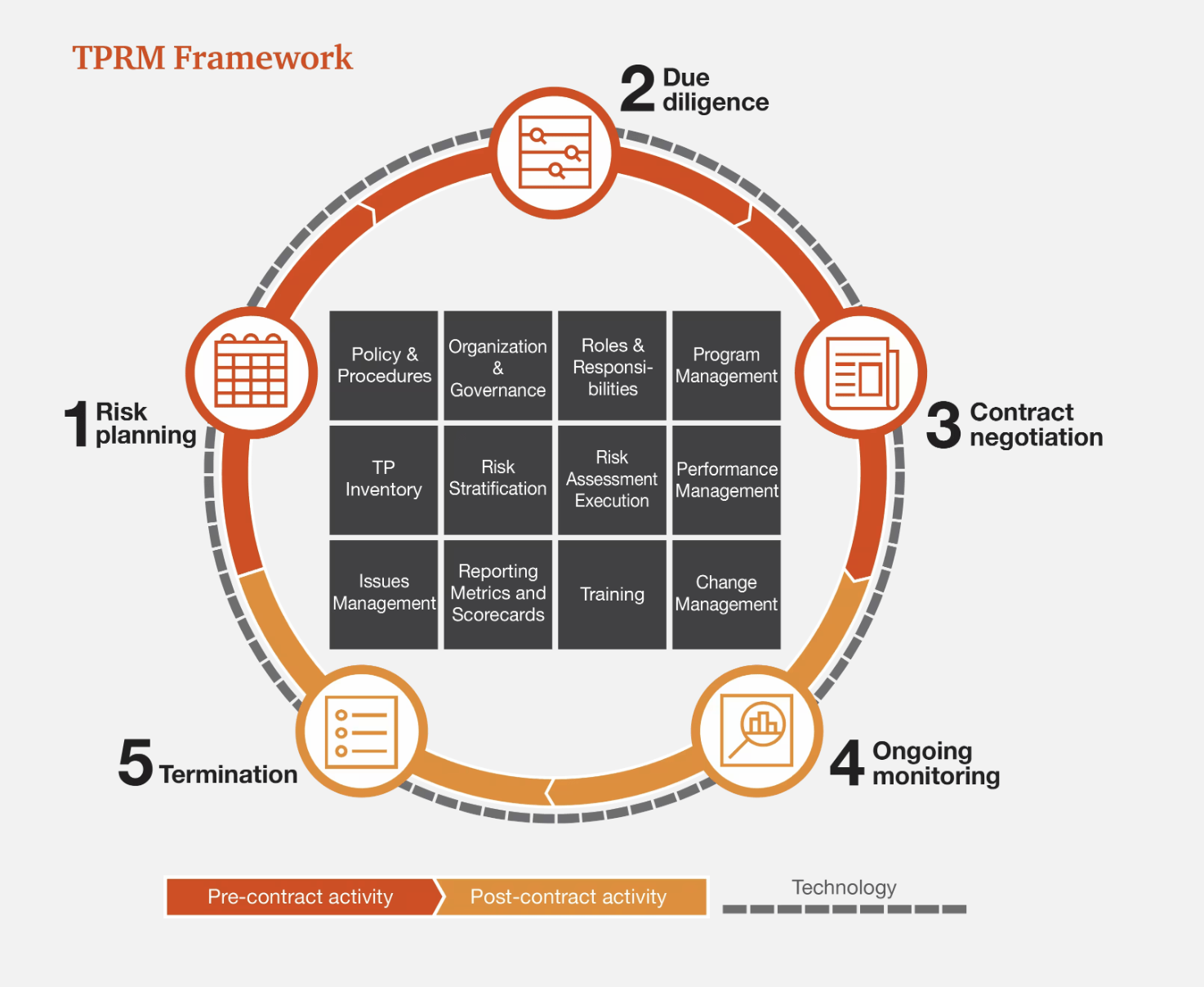
Third-Party Risk Management and ongoing vendor risk management is used interchangeably. Both vendor assessment and TPRM involves identifying, assessing, and controlling risks that occur due to interactions with third parties. TPRM governs the whole process, including onboarding, ongoing management and monitoring and off-boarding and might involve other potential risks such as financial risks, operational risks, etc.
Vendor Assessment And The GDPR
Under the GDPR Article 28(1):
‘the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organisational measures in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject’.
Therefore, data controllers are responsible for ensuring that third-party data processors comply with strict data protection requirements. Furthermore, Once the vendor assessment process is complete, don’t forget that in accordance with GDPR Article 28(3):
‘processing by a processor must be governed by a contract or other legal act under Union or Member State law ’
When a contract is signed with a data processor, tt is usually referred to as a ‘Data Processing Addendum’ or DPA . The contract should include specific clauses that outline the data controller’s responsibilities and confidentiality obligations, as well as the requirement to process data in accordance with the controller’s instructions.
What Does It Mean In Practice?
In order to make sure that this is the case, a data controller must follow procedures known as vendor privacy due diligence or vendor privacy assessment.
By conducting vendor assessment, companies can ensure compliance with the GDPR and minimize data breach risks by assessing the data processing activities of their potential risks.
Vendor due-diligence (or vendor assessment), assists the company in maintaining regulatory compliance, but also ensures the protection of customer data and thus protects the company’s reputation.
How To Conduct Privacy Assessment Regarding Data Privacy?
When you perform a third-party or a vendor assessment, you determine the most likely outcomes of uncertain events, then you determine their importance, measure them, and prioritise them.
Key methods to assess while conducting a vendor privacy assessmentL
- Review public policies – This includes privacy policies, online data processing addendum (if applicable), incident handling procedures, data subject rights processes, and security measures (such as Technical and Organisational Measures). This will help you understand how personal data will be handled, for what purposes, and it would provide details on international data transfers.
- Be consistent and comprehensive – It’s important to have a consistent method of vendor privacy assessment in place and document the process. This will ensure that all vendors are treated equally and that all risks are identified and mitigated. Additionally, documenting the process will provide a clear audit trail that can be used in the event of a breach or other incident.
- Consider a variety of risks – Such as the types of data the vendor has access to, the location of processing, the mechanisms of transfer, the retention periods, security breaches, data subject rights, incident response procedures, legal and regulatory compliance, and many others.
This is usually done by sending out privacy and security questionnaires. However, this process is long and tiresome for both sides. Instead, you can look up your potential vendor on TrustHub and get a detailed risk profile, free of charge.
Key Timeframes For Vendor Assessment
Along with ongoing vendor management and risk monitoring, it is essential to conduct vendor assessments during onboarding and off-boarding.
It is essential to verify that the vendor has adequate privacy and security practices in place before onboarding them. Otherwise, your company may be exposed to risks, breaches and brand damage.
Any small change in policy or subprocessor may trigger a new assessment of the vendor once the vendor is already being used. Hence, even once the vendor is in use, it is important to continuously monitor the vendor for changes and potential privacy risks.
Off-boarding a vendor requires verifying whether data has been deleted, returned or destroyed according to the agreement. Otherwise, your company might be at risk in the future if the vendor suffers a data breach.
Vendor Risk Monitoring
In order to mitigate privacy risks, you should perform vendor due diligence and monitor your vendors (particularly those who process personal data) if you wish to build a strong foundation for a productive relationship. In particular, it’s important to monitor:
- Changes to subprocessors
- Changes to policies
- Transfer of processing to a new location
- Data breach
- Data Protection Authorities’ investigations or inquiries

Don't let your vendors risk you
Conclusion
Vendor Assessments evaluate how vendors handle the personal data that companies share with them. This helps determine whether vendors are maintaining adequate security and privacy controls. Under the GDPR, data controllers must ensure that third-party data processors comply with strict data protection requirements. To do this, they must conduct vendor due diligence (or vendor assessment), which involves assessing the data processing activities of their potential risks.

Noa Kahalon
Noa is a certified CIPM, CIPP/E, and a Fellow of Information Privacy (FIP) from the IAPP. Her background consists of marketing, project management, operations, and law. She is the co-founder and COO of hoggo, an AI-driven SaaS platform for B2B trust where sellers can showcase & improve compliance and buyers can evaluate, manage and monitor them.